Compare ISO 27001:2013 to ISO 27001:2022
The new version of ISO 27001 was published in October of 2022. Although the changes from the 2013 version are not drastic, they are still worth reviewing. We have prepared a detailed 10 page document comparing the changes from ISO 27001:2013 to ISO 27001:2022 (sign up below for this free document). We have also prepared a general comparison (see below).
For a DETAILED comparison, sign up for our newsletter and receive a free 10-page download!
Enter your email, and we will send a confirming email with a link to download.
Find Information Security Manual & Procedures package and other products here
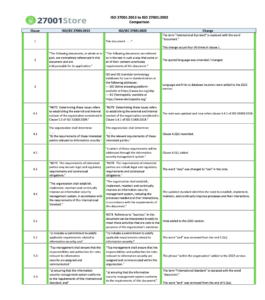
Compare ISO 27001: 2013 vs 2022
| ISO 27001:2013 | ISO 27001:2022 |
| Introduction | Introduction |
| 1 Scope | 1 Scope |
| 2 Normative references | 2 Normative references |
| 3 Terms and definitions | 3 Terms and definitions |
| 4 Context of the Organization | 4 Context of the Organization |
| 4.1 Understanding the organization and its context | 4.1 Understanding the organization and its context |
| 4.2 Understanding the needs and expectations of interested parties | 4.2 Understanding the needs and expectations of interested parties |
| 4.3 Determining the scope of the information security management system | 4.3 Determining the scope of the information security management system |
| 4.4 Information security management system | 4.4 Information security management system |
| 5 Leadership | 5 Leadership |
| 5.1 Leadership and Commitment | 5.1 Leadership and Commitment |
| 5.2 Policy | 5.2 Policy |
| 5.3 Organization roles, responsibilities, and authorities | 5.3 Organization roles, responsibilities, and authorities |
| 6 Planning | 6 Planning |
| 6.1 Actions to address risks and opportunities | 6.1 Actions to address risks and opportunities |
| 6.1.1 General | |
| 6.1.2 Information security risk assessment | |
| 6.1.3 Information security risk treatment | |
| 6.2 Information Security objectives and planning to achieve them | 6.2 Information Security objectives and planning to achieve them |
| 7 Support | 7 Support |
| 7.1 Resources | 7.1 Resources |
| 7.2 Competence | 7.2 Competence |
| 7.3 Awareness | 7.3 Awareness |
| 7.4 Communication | 7.4 Communication |
| 7.5 Documented information | 7.5 Documented information |
| 7.5.1 General | |
| 7.5.2 Creating and updating | |
| 7.5.3 Control of documented information | |
| 8 Operation | 8 Operation |
| 8.1 Operational planning and control | 8.1 Operational planning and control |
| 8.2 Information security risk assessment | 8.2 Information security risk assessment |
| 8.3 Information security risk treatment | 8.3 Information security risk treatment |
| 9 Performance evaluation | 9 Performance evaluation |
| 9.1 Monitoring measurement, analysis and evaluation | 9.1 Monitoring measurement, analysis and evaluation |
| 9.2 Internal audit | 9.2 Internal audit |
| 9.2.1 General | |
| 9.2.2 Internal audit programme | |
| 9.3 Management review | 9.3 Management review |
| 9.3.1 General | |
| 9.3.2 Management review inputs | |
| 9.3.3 Management review outputs | |
| 10 Improvement | 10 Improvement |
| 10.1 Nonconformity and corrective action | 10.1 Continual improvement |
| 10.2 Continual improvement | 10.2 Nonconformity and corrective action |
| Annex A – directly derived from and aligned with controls listed in ISO/IEC 27002:2013 and shall be used in context with Clause 6.1.3 | Annex A – directly derived from and aligned with controls listed in ISO/IEC 27002:2013 and shall be used in context with Clause 6.1.3 |
| 114 controls divided into 14 chapters (clauses 5-18) | 93 controls, divided into 4 chapters (clauses 5-8) Some controls look new and others have been merged. |